华为企业网络配置示例2,旁挂三层直接转发
来源:原创
时间:2024-04-25
作者:脚本小站
分类:网络
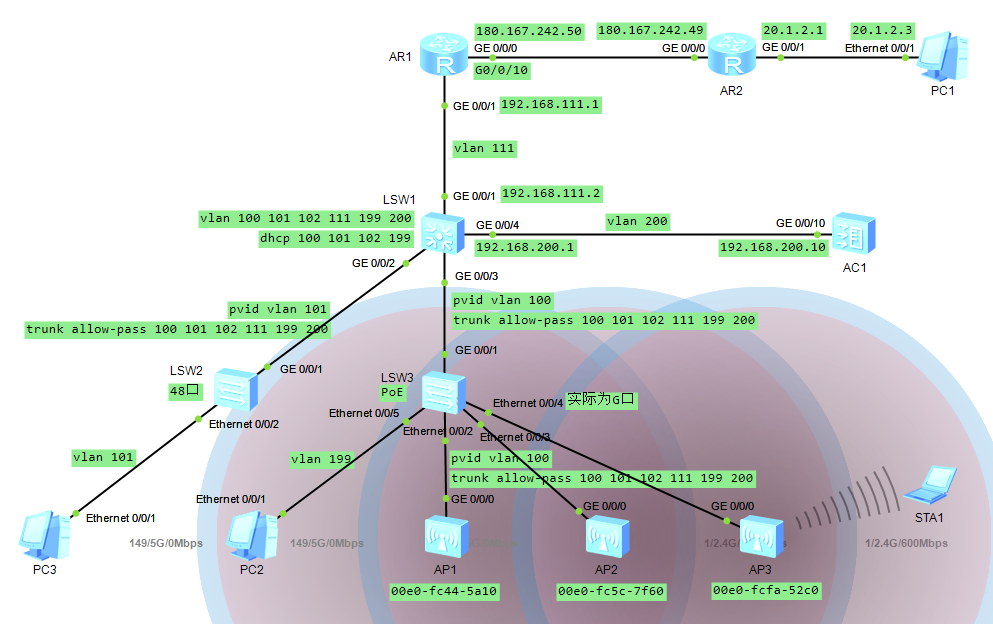
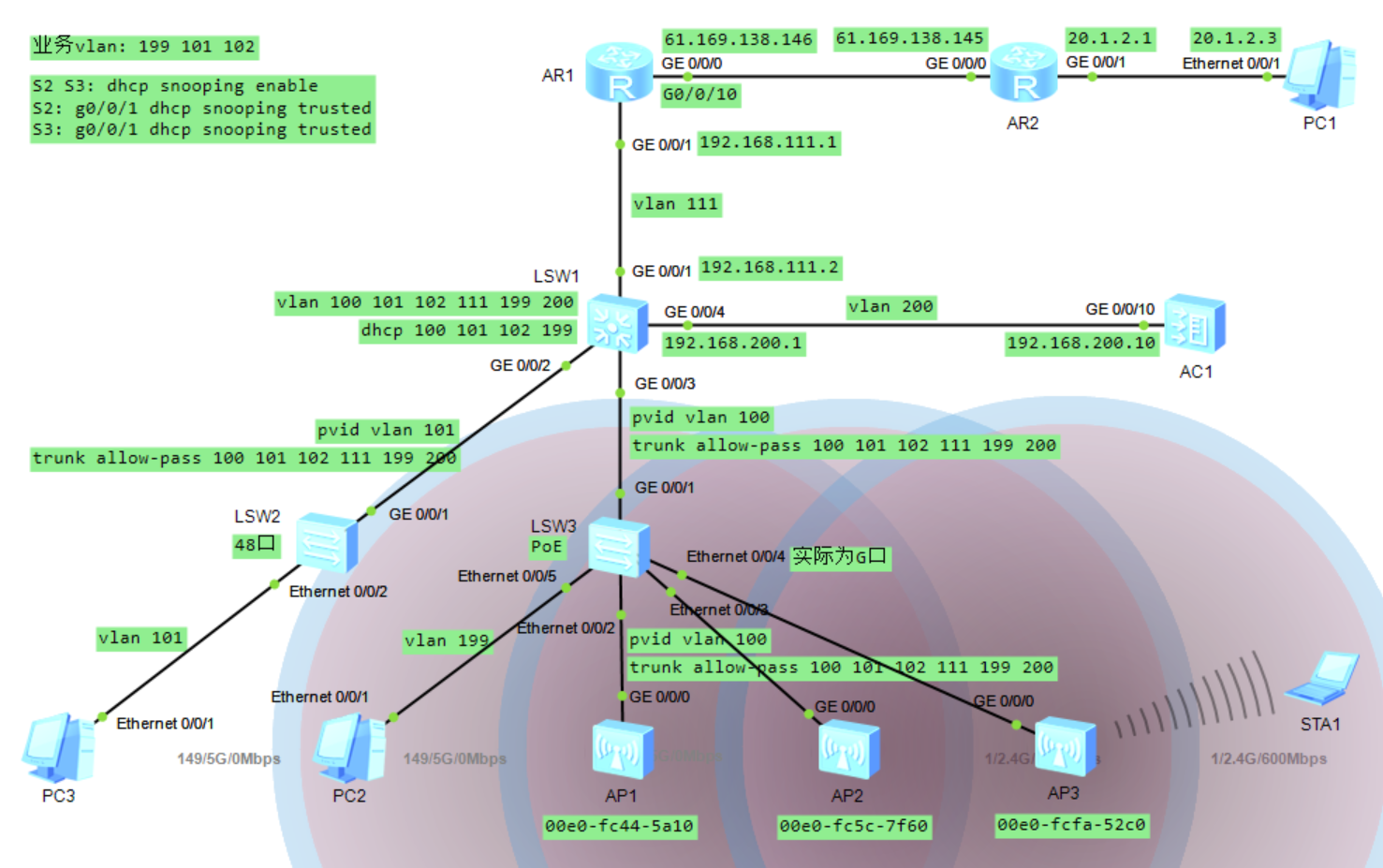
AR1-----------------单出口ip配置------------------ interface GigabitEthernet 0/0/1 undo portswitch ip address 192.168.111.1 24 quit # 实物机wan口为10口 interface GigabitEthernet 0/0/10 ip address 180.167.242.50 24 quit ip route-static 192.168.0.0 16 192.168.111.2 ip route-static 0.0.0.0 0 180.167.242.49 # nat acl 2000 rule 5 permit source 192.168.101.0 0.0.0.255 rule 6 permit source 192.168.102.0 0.0.0.255 rule 7 permit source 192.168.199.0 0.0.0.255 rule 10 deny # 如果端口处于down状态则ping不通 interface GigabitEthernet 0/0/10 nat outbound 2000 AR1----------------多出口ip配置------------------- interface GigabitEthernet 0/0/1 undo portswitch ip address 192.168.111.1 24 quit ip route-static 192.168.0.0 16 192.168.111.2 ip route-static 0.0.0.0 0 61.169.138.145 acl 2000 rule 5 permit source 192.168.101.0 0.0.0.255 rule 6 permit source 192.168.102.0 0.0.0.255 rule 7 permit source 192.168.199.0 0.0.0.255 rule 10 deny nat address-group 1 61.169.138.147 61.169.138.149 interface GigabitEthernet 0/0/10 ip address 61.169.138.146 255.255.255.248 nat outbound 2000 address-group 1 ------ NAT Server 配置 ------ interface GigabitEthernet 0/0/10 nat server protocol tcp global 61.169.138.150 666 inside 192.168.199.6 443 # 此时只能在外部地址才能访问 # 需要同时在下行接口配置nat,将内部主机使用公网IP地址访问服务器的流量,引到Router上进行NAT转换 acl 3000 rule 5 permit ip source 192.168.0.0 0.0.255.255 destination 61.169.138.150 0 # 配置上如下规则,内网才能通过公网IP访问内网服务 interface GigabitEthernet0/0/1 nat outbound 3000 nat server protocol tcp global 61.169.138.150 666 inside 192.168.199.6 443 S1------------------------------------------------ vlan batch 100 101 102 111 199 200 dhcp enable ip pool vlan100 network 192.168.100.1 mask 24 gateway-list 192.168.100.1 option 43 sub-option 3 ascii 192.168.200.10 quit ip pool vlan101 network 192.168.101.1 mask 24 gateway-list 192.168.101.1 dns-list 114.114.114.114 quit ip pool vlan102 network 192.168.102.1 mask 24 gateway-list 192.168.102.1 dns-list 114.114.114.114 quit ip pool vlan199 network 192.168.199.1 mask 24 gateway-list 192.168.199.1 dns-list 114.114.114.114 quit interface Vlanif 100 ip address 192.168.100.1 24 dhcp select global quit interface Vlanif 101 ip address 192.168.101.1 24 dhcp select global quit interface Vlanif 102 ip address 192.168.102.1 24 dhcp select global quit interface Vlanif 111 ip address 192.168.111.2 24 quit interface Vlanif 199 ip address 192.168.199.1 24 dhcp select global quit interface Vlanif 200 ip address 192.168.200.1 24 quit interface GigabitEthernet 0/0/1 port link-type access port default vlan 111 quit interface GigabitEthernet 0/0/2 port link-type trunk port trunk pvid vlan 101 port trunk allow-pass vlan 100 101 102 111 199 200 quit interface GigabitEthernet 0/0/3 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 101 102 111 199 200 quit interface GigabitEthernet 0/0/4 port link-type access port default vlan 200 quit ip route-static 0.0.0.0 0 192.168.111.1 S2------------------------------------------------ vlan batch 100 101 102 111 199 200 interface GigabitEthernet 0/0/1 port link-type trunk port trunk pvid vlan 101 port trunk allow-pass vlan 100 101 102 111 199 200 quit interface Ethernet 0/0/2 port link-type access port default vlan 101 quit # dhcp snooping dhcp enable dhcp snooping enable interface GigabitEthernet0/0/1 dhcp snooping trusted quit S3------------------------------------------------ vlan batch 100 101 102 111 199 200 interface GigabitEthernet 0/0/1 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 101 102 111 199 200 quit port-group port2-4 group-member Ethernet 0/0/2 to Ethernet 0/0/4 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 101 102 111 199 200 quit interface Ethernet 0/0/5 port link-type access port default vlan 199 quit # dhcp snooping dhcp enable dhcp snooping enable interface GigabitEthernet0/0/1 dhcp snooping trusted quit AC1------------------------------------------------ vlan batch 200 interface Vlanif 200 ip address 192.168.200.10 24 quit interface GigabitEthernet 0/0/10 port link-type access port default vlan 200 quit ip route-static 0.0.0.0 0 192.168.200.1 # 记得在管理vlan加上如下选项 [S1-ip-pool-vlan100]option 43 sub-option 3 ascii 192.168.200.10 # 关闭dtls capwap dtls no-auth enable capwap source interface Vlanif 200 wlan regulatory-domain-profile name default country-code cn ap-group name tanzhi regulatory-domain-profile default ap auth-mode mac-auth ap-id 1 ap-mac f83e-9557-dec0 ap-name ap1 ap-group tanzhi ap-id 2 ap-mac f83e-9557-e840 ap-name ap2 ap-group tanzhi ap-id 3 ap-mac 2841-ec8d-c680 ap-name ap3 ap-group tanzhi ssid-profile name ssidtanzhi ssid tanzhishuju-wifi1 security-profile name sectanzhi security wpa-wpa2 psk pass-phrase tanzhi2017 aes vap-profile name vaptanzhi forward-mode direct-forward service-vlan vlan-id 101 ssid-profile ssidtanzhi security-profile sectanzhi ap-group name tanzhi vap-profile vaptanzhi wlan 1 radio 0 vap-profile vaptanzhi wlan 1 radio 1 # 添加第二个vap ssid-profile name ssidguest ssid tanzhishuju-guest quit security-profile name secguest security wpa-wpa2 psk pass-phrase tanzhi2017 aes quit vap-profile name vapguest forward-mode direct-forward service-vlan vlan-id 102 ssid-profile ssidguest security-profile secguest quit ap-group name tanzhi vap-profile vapguest wlan 2 radio 0 vap-profile vapguest wlan 2 radio 1
注意点:DTLS是安全方面的东西,执行 capwap dtls no-auth enable 命令关闭即可,但是密码需要设置下,根据流程走即可。
[AC1]capwap source interface vlanif 200 Set the DTLS PSK(contains 8-32 plain-text characters, or 48 or 68 cipher-text characters that must be a combination of at least two of the following: lowercase letters a to z, uppercase letters A to Z, digits, and special characters): Confirm PSK: Configuring the new PSK, waiting... Info: Deliver DTLS PSK to devices using CAPWAP connections. It may take a few minutes. ------------------------------------------------------------------------------ CAPWAP DTLS PSK deliver result Deliver Number : 0 Success Number : 0 Failed Number : 0 ------------------------------------------------------------------------------...................done. Set the DTLS inter-controller PSK(contains 8-32 plain-text characters, or 48 or 68 cipher-text characters that must be a combination of at least two of the following: lowercase letters a to z, uppercase letters A to Z, digits, and special characters): Confirm PSK: Configuring the new PSK, waiting......................done. Set the user name for FIT APs(The value is a string of 4 to 31 characters, which can contain letters, underscores, and digits, and must start with a letter):admin Set the password for FIT APs(plain-text password of 8-128 characters or cipher-text password of 48-188 characters that must be a combination of at least three of the following: lowercase letters a to z, uppercase letters A to Z, digits, and special characters): Confirm password: Set the global temporary-management psk(contains 8-63 plain-text characters, or 48-108 cipher-text characters that must be a combination of at least two of the following: lowercase letters a to z, uppercase letters A to Z, digits, and special characters): Confirm PSK: Warning: Ensure that the management VLAN and service VLAN are different. Otherwise, services may be interrupted. Warning: Before an added device goes online for the first time, enable DTLS no-auth if it runs a version earlier than V200R021C00 or enable DTLS certificate-mandatory-match if it runs V200R021C00 or later. [AC1]
配置AC遇到的问题:
AP为idle状态:
[AC1-wlan-view]display ap all ----------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime ExtraInfo ----------------------------------------------------------------------------- 1 f83e-9557-dec0 ap1 tanzhi - - idle 0 - - 2 f83e-9557-e840 ap2 tanzhi - - idle 0 - - 3 2841-ec8d-c680 ap3 tanzhi - - idle 0 - - ----------------------------------------------------------------------------- Total: 3
核心交换机上:查看mac地址是否有AP设备的,如果AP对应的MAC地址获取到了IP,则请看下一步。
[S1]display arp all IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE VLAN ------------------------------------------------------------------------------ 192.168.100.1 3cc7-8688-23db I - Vlanif100 192.168.100.205 f83e-9557-dec0 10 D-0 GE0/0/3 100 192.168.100.115 2841-ec8d-c680 17 D-0 GE0/0/3 100 192.168.100.213 f83e-9557-e840 17 D-0 GE0/0/3 100 192.168.101.1 3cc7-8688-23dc I - Vlanif101 192.168.102.1 3cc7-8688-23dd I - Vlanif102 192.168.111.2 3cc7-8688-23d7 I - Vlanif111 192.168.111.1 28fb-ae19-67ae 16 D-0 GE0/0/1 111 192.168.199.1 3cc7-8688-23d5 I - Vlanif199 192.168.200.1 3cc7-8688-23d6 I - Vlanif200 192.168.200.10 28fb-ae50-ffed 16 D-0 GE0/0/4 200 ------------------------------------------------------------------------------ Total:11 Dynamic:5 Static:0 Interface:6
到AC上面,ping AP的地址,是可以ping通的。
<AC1>ping 192.168.100.205 PING 192.168.100.205: 56 data bytes, press CTRL_C to break Reply from 192.168.100.205: bytes=56 Sequence=1 ttl=254 time=2 ms Reply from 192.168.100.205: bytes=56 Sequence=2 ttl=254 time=2 ms
查看AP没有上线成功的原因,是因为没有导入license文件,需要导入license文件。
<AC1>display ap online-fail-record all ------------------------------------------------------------------------------ MAC Last fail time Reason ------------------------------------------------------------------------------ 2841-ec8d-c680 2024-04-28/11:24:19 Insufficient license resources f83e-9557-dec0 2024-04-28/11:25:01 Insufficient license resources f83e-9557-e840 2024-04-28/11:24:58 Insufficient license resources ------------------------------------------------------------------------------ Total APs: 3 Total records: 3
获取license文件:
license文件需要授权码,授权码在pdf里面,这个pdf文件在购买设备时商家会发送给你,将授权码或PDF文件和设备上的ESN码,
发送给华为的邮箱 license@huawei.com 来获取 license 文件,过一段时间对方会回邮件,邮件附件中带有 LICWAC-S_V200R022_XXXXX0000.dat 的文件,将这个文件通过AC的web页面导入即可。
或者通过如下地址去获取,跟客服区沟通即可。
https://support.huawei.com/livechat/license
ESN码的获取:这个ESN码是AC上的ESN码,在AC上输入如下命令。
<AC1>display sn license Equipment SN(ESN): 111111111111 <AC1>display license esn Master ESN is: 11111111111.
导入license文件:
AC上,查看vlan1的IP地址
<AC1>display ip interface brief Interface IP Address/Mask Physical Protocol Ethernet0/0/47 169.254.3.1/24 up up NULL0 unassigned up up(s) Vlanif1 169.254.1.1/24 down down Vlanif200 192.168.200.10/24 up up
将电脑设置为vlanif1同样的地址段,网线接入AC中的任意接口,浏览器中输入 https://169.254.1.1 即可登陆到web页面,在web页面中->维护->AC维护->License管理->License文件信息,找到位置导入即可。
AP为unauth状态:
[AC1-wlan-view]display ap all Total AP information: unauth: unauthed [3] ExtraInfo : Extra information ----------------------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime ExtraInfo ----------------------------------------------------------------------------------------- - f83e-9557-e840 - - - AirEngine5762S-12 unauth - - - - 2841-ec8d-c680 - - - AirEngine5762S-12 unauth - - - - f83e-9557-dec0 - - - AirEngine5762S-12 unauth - - - ----------------------------------------------------------------------------------------- Total: 3
这种状态是AP加入了AC,还需要确认:
[AC1-wlan-view]ap-confirm all Info: This operation may take a few seconds. Please wait for a moment.done. Info: Confirm AP completely. Run the "display ap unauthorized record" command to check the result. [AC1-wlan-view]display ap unauthorized record Info: There is no ap unauthorized record.
参考文档:
https://support.huawei.com/hedex/hdx.do?docid=EDOC1100096148&id=ZH-CN_TASK_0176912356
配置完成后:
[AC1]display ap all Total AP information: nor : normal [3] ExtraInfo : Extra information ---------------------------------------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime ExtraInfo ---------------------------------------------------------------------------------------------------------- 1 f83e-9557-dec0 ap1 tanzhi 192.168.100.205 AirEngine5762S-12 nor 0 2H:2M:50S - 2 f83e-9557-e840 ap2 tanzhi 192.168.100.213 AirEngine5762S-12 nor 0 2H:4M:24S - 3 2841-ec8d-c680 ap3 tanzhi 192.168.100.115 AirEngine5762S-12 nor 0 2H:3M:48S - ---------------------------------------------------------------------------------------------------------- Total: 3 [AC1]display vap all Info: This operation may take a few seconds, please wait. WID : WLAN ID --------------------------------------------------------------------------------------- AP ID AP name RfID WID BSSID Status Auth type STA SSID --------------------------------------------------------------------------------------- 1 ap1 0 1 F83E-9557-DEC0 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 1 ap1 0 2 F83E-9557-DEC1 ON WPA/WPA2-PSK 0 tanzhishuju-guest 1 ap1 1 1 F83E-9557-DED0 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 1 ap1 1 2 F83E-9557-DED1 ON WPA/WPA2-PSK 0 tanzhishuju-guest 2 ap2 0 1 F83E-9557-E840 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 2 ap2 0 2 F83E-9557-E841 ON WPA/WPA2-PSK 0 tanzhishuju-guest 2 ap2 1 1 F83E-9557-E850 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 2 ap2 1 2 F83E-9557-E851 ON WPA/WPA2-PSK 0 tanzhishuju-guest 3 ap3 0 1 2841-EC8D-C680 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 3 ap3 0 2 2841-EC8D-C681 ON WPA/WPA2-PSK 0 tanzhishuju-guest 3 ap3 1 1 2841-EC8D-C690 ON WPA/WPA2-PSK 0 tanzhishuju-wifi1 3 ap3 1 2 2841-EC8D-C691 ON WPA/WPA2-PSK 0 tanzhishuju-guest ---------------------------------------------------------------------------------------
